Case study – extinguishing SparkOnSoft malware
Intro
In the past week we’ve seen a surge with new variants of a malware which our Active Ransomware Prevention platform prevented for multiple customers worldwide.
The common thread between all the attacks is the source, all are installations of a supposed PDF application called PDF SparkOnSoft.
Entry Point
In all cases the files were download from online, suggesting the scammers placed malicious ads and/or poisoned chat-based AIs to appear legitimate.
Basic Information
The file is a small installer written with InnoSetup as it contains details related to a PDF app.
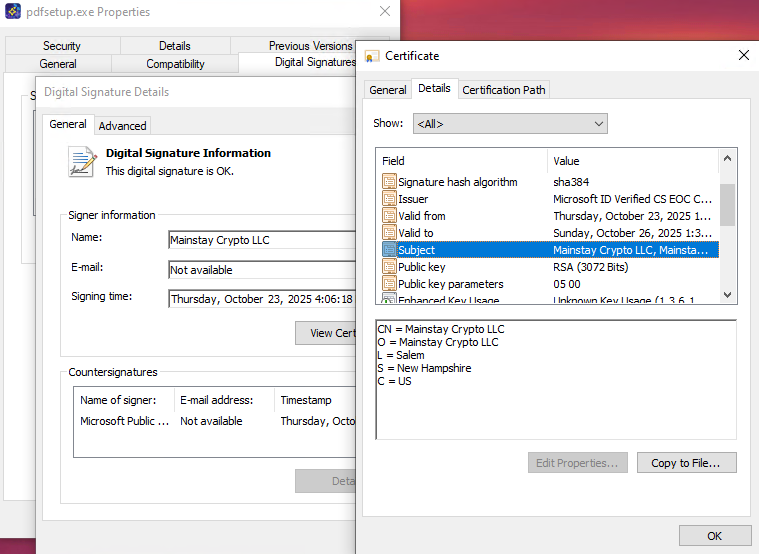
The first payload our solution prevented was signed with an Extended Validation certificate by Mainstay Crypto LLC and issued by Sectigo.
The other installers were signed by the same vendor, however, this time the certificate was issued by Microsoft.
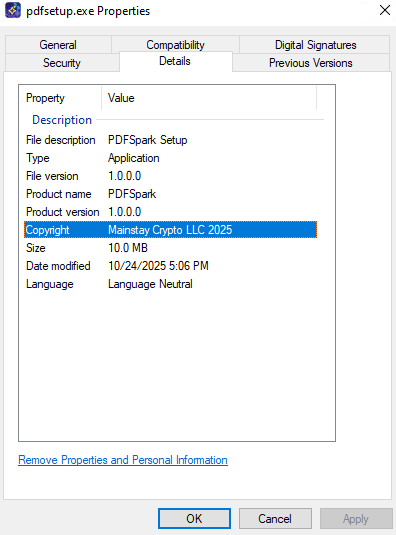
The file’s properties indicate that it’s a PDF software and the publisher as Mainstay Crypto.
The version remains 1.0.0.0 between samples as the attackers likely didn’t modify the InnoSetup installer used for building the malicious payload.
Execution
When executed, all the samples first checks if they’re running under WINE, a Windows compatibility-layer that allows Windows PE executables to run under Linux, macOS and other non-Windows operating systems, they do so by checking if the function wine_get_version exists in ntdll.dll, Windows’ Native API dynamic library, as this function only exists in WINE environments
(Microsoft’s ntdll file never had this exported function).
Prevention
Since the above execution is a clear indication of a malicious activity as attackers check for WINE to identify being investigated by security services utilizing WINE for malware analysis, the Deceptive Bytes platform immediately stopped the attack and all the malware samples failed to infect our customers’ machines.
IOCs
- SHA2: 415b6d1bb78cb74a468b29e7af09e885999cfcabf2c413f3bf533c2191d4e626
- SHA2: 4617e321a142d4ed35d71d3532be764deec63dafe8bdec010a8ace4ea5bba5b4
- SHA2: 00f0338e7caa630d10347a5bebed83bb4c11ebce34f4470a213f93828a66addf
- SHA2: 717c2728b957a7faecb7d1ac057bb03053f6397bbc369092c493daf6d45dc67c
- SHA2: c1f686082eb39db8cd58f36247e894b22c95d10672e9d50380b824ab9f2e2f46 (installer payload)
- Imphash: efd455830ba918de67076b7c65d86586
- Certificates: Mainstay Crypto LLC
- Issuer #1: Sectigo Public Code Signing CA EV R36 (now revoked)
- Issuer #2: Microsoft ID Verified CS EOC CA 02 (still valid)
- Compromising website: hxxps://sparkonsoft[.]com
- Compromised AWS S3: hxxps://pdfsparkcomponent[.]s3.us-east-2.amazonaws.com
Don’t Miss a Thing
Sign up today and we’ll send an email when new posts come out.
We collect and use this information in accordance with our privacy policy.

